With the release of VMware vCenter Server 5.1 an important new component has been released: the VMware Single Sign-On (SSO) server. It is one of the components of vCenter Server and is a requirement for installation. Through the SSO server a user now gets authenticated and receives a token that authenticates the user with other vCenter components without having to Sign-On again.
Some users ran into some minor issues when installing SSO. Most common issue is “Error 29115 Cannot authenticate to DB”. An error which I encountered myself was “Error 29155 Identity source discovery error”. According to KB 2034374 this is due to a failed attempt to automatically discover an Active Directory domain. You can click OK on this error and continue installation. Before installing the vCenter Server component it is adviced to manually add Active Directory Authentication to SSO.
Take the following steps:
- Log in to the vSphere Web Client: https://<ip addres>:9443/vsphere-client using the basic SSO account. For a Windows install of SSO this is the user “admin@System-Domain” and for the vCenter Server Virtual Appliance it is “root@System-Domain”. The password is what you have entered during installation of SSO.
- Go to the section Administration – Sign-On Discovery. In the middle of the screen you’ll now see the identity sources that are already present.
- To add Active Directory if this was not already present, click the red plus sign in the middle upper menu bar.
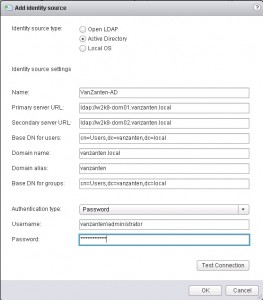
- In the pop-up window select “Active Directory” and fill out the form.
For my homelab environment the domain name is “vanzanten.local”, the primary and secondary URL are references to both my domain controllers. The Base DN users is the OU where the default users reside, which in my case is the same as the Base DN groups. Domain name is the FQDN and domain alias is the Netbios name of your Active Directory domain. The last section is the user account you will use to query the AD. Since it is just a home lab I use my administrator account for this. Press “Test Connection” to make sure your connection details are valid.
Still under investigation: In my test it seems that entering different values for Group and User Base DN is not working correctly. Either an interface error or a bug, but when using two different values, after saving and then editing again, both values are identical.
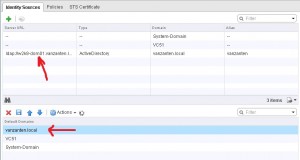
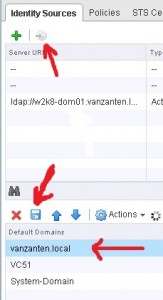
After you have a successful connection, click OK and you’ll see your newly created Identity Source. Next add the new identity source to the default domains by clicking “Add to default domains” in the top bar. Now your identity source will show in the lower screen. Set it to the first in the list using the arrows and DON’T forget to press SAVE.
Hiya Gabie,
I also ran into loads of 29155 Error Identifying source authority.
I followed the KB article and I also compared the settings with another working SSO.
The Base DN it does not need t go down to CN=Users,DC=domain,DC=com just DC=domain,DC=com should work.
Great addition, thank you!
Excellent post! Thanks for the info.
Have any luck joining a separate vcenter to a multisite SSO config? Trying to for SRM build but failing on login to SSO?
“. Before installing the vCenter Server component it is adviced to manually add Active Directory Authentication to SSO.
Take the following steps:
Log in to the vSphere Web Client:”
Can you tell me how you login to vcenter with vsphere web client without installing vcenter ? o_O
The name is vSphere Web Client and not vCenter Web Client. You are no longer directly logging into vCenter, but into the SSO Server. The SSO server will authenticate you and offer components you can go to. One of them is the vCenter Server.
Ok so installing the vsphere web client server first, then doing the steps u say in the article, and then installing vcenter server, right ?
Yes. Do keep in mind that my post is not needed when your vCenter to-be-server is already member of the AD. Then just follow the manual.
Oh, ok, because my future vcenter-server is already in domain but I got the error.
I ll follow your tutorial and see what authentification sources are already present then.
Ok finally I HAD to add the AD source because it was not present whereas the server was in AD. So I guess anyone who got this error should follow your guide.
Also using domainusername as username didn’t work for me, but username@domain did.
so If I don’t do this SSO thing my AD users won’t be able to login?
Without SSO you can’t access vCenter at all.
it worked like a charm.thanks a lot buddy!
Thank you so much for posting this. I have been struggling with this for a couple of days. This really solved my problem.
I’ve a separate service account created for vcenter installation & I’m using that account throughout while using the same account for password authentication gives me an error [LDAP: error code 49 – 80090308: LdapErr:
DSID-0C090334, comment: AcceptSecurity Context error, data 52e, vece] . Per the FAQ on VMware it says the account should have read-only rights to Base DN while I tried providing the read-only rights even to the root on my AD but it still fails.
When I try to perform test authentication with a Domain Admin rights it does work though I cannot use that for this purpose. Does any one knows what exact rights are required for the username on AD so that test authentication goes successful?
Actually I though all accounts by default are able to enumerate users from AD by querying the AD. Only limit would be 1000 records per query, but that also goes for the admin account which you said does work. Can you check the security log on the Domain Controller to see why it is blocking the user from performing the query?
Another thing I just thought of, do you have admin access to the AD to create a new user account with ‘default’ permissions and see if that works? I would suspect that the original account your trying has his permissions blocked on purpose.
Hello, great article thanks. My AD is discovered and ‘Test Connection’ returns successfully. But no AD accounts are populating in the ‘Users’ section under SSO users and groups. Strangely though….disabled AD accounts are populating in the ‘Disabled Users’ section. I try changing the base DN to a different OU etc and no change (just get the disabled accounts from that OU populate). Any ideas?
Hi
Users are not automatically populated. You have to search for a user or group and then add them. So SSO will not show a copy of the complete AD user list
Gabrie
Hi Gabrie,
I’m having trouble with losing all of my domain permissions on the database upgrade even when adding in the AD manually before the upgrade.
It tests fine and I see users in the disabled area.
Any way to keep the current permissions I had set before the upgrade?
Thanks,
Jim
Not sure if I understand what you’re saying. Do you mean permissions you granted to users in vCenter 4 are lost when upgrading to vCenter 5? Never tested that to be honest.
Bedankt! Wist even niet meer wat ik moest doen en toe kwam ik je post tegen. Super!
Thanks a lot man…it really worked..!
Thanks a lot mate.
Thank you so much.
Great Post. Worked for me also when specified username in username@domain format
thank you where much.
Thank you for this great post.
You mentioned this:
“Still under investigation: In my test it seems that entering
different values for Group and User Base DN is not working correctly.
Either an interface error or a bug, but when using two different values,
after saving and then editing again, both values are identical.”
That is my issue as well. The problem is, the users that need to log into the web client are NOT in the users OU, so they can’t log in. Of course, any user I add to the _admin_ group can log in without issue (as they are in the users OU). Did you ever figure this problem out?
Hi Angela, Haven’t discovered why this happens. I think you need to make a support call with VMware for this.
LERN ENGRISH, U FOKEN FAGHOST!!!!!!
Hi,
First, thanks for your post.
It have still som equestion on ldap/vmware configuration.
My problem is, i don’t want to select user by user into permission tab in SSO.
I had a ldap organisation like “ou=VMWARE,ou=UserGroups,ou=Groups,dc=prd,dc=mut,dc=com
Into the VMWARE “ou” i’ve got 2 groups “system” and “network”.
I’ve got another system to populate this groups into the AD and i would like to associate ldap groups (where my user account is) and vmware groups/roles.
But SSO cannot recognize my user who is in this group so i cannot connect to my vCenter instance.
Do you have an idea ?
Thanks ! :)
Send me an e-mail and I’ll help you figure this out for your environment. (Sorry for the late response)
Hola,
Gracias por tu aportación
me fue de mucha ayuda
Saludos
A very clear explanation and screen shots, bravo and thanks a lot.
Ami
Clear and concise. Awesome instructions!
worked like a champ. Thanks!!!!!!!!
Exactly what I was looking for…thanks for the explanation/screenshots!!
yesssss!!!! got it!!!!!!!!!!! Exactly I was looking for … special thanks!!!!!!
Thanks, worked great
Thank youuuuuuu great post:)
Many thanks:)
nice … worked a treat
I’ve seen a ton of people on multiple posts around the web that indicated they were having issues with everything checking back OK when creating the Identity Source but the usernames and groups will not populate when trying to add permissions to the host or to VCenter.
The fix for me was as simple as changing the Identity Source to use “Active Directory” rather than “Open LDAP”. If you already created the Identity Source then you will have to delete the LDAP version and create a new Identity Source with the “Active Directory” option selected at the top of the “Add Identity Source” window.
Side note:
Make sure you check the Domain Alias to see if it is different from your Domain Name.
Example:
Domain name = Company.local
Domain alias = Comp
To verify, go to the properties of your domain (company.local) in Active Directory. The Domain name (pre-Windows 2000) section will tell you your proper NetBIOS name.
cheers bro
I Have got Couple of doubts .
1. How would you verify that single sign on is properly installed on the vCenter server for 5.1 version?
2. I am now authenticating users to login to my vCenter with one Domain credentials, Can i permit users from other domain to login ?? if so how? and also do we have a fault tolerence for the vCenter (in the sense if the vCenter crashes other vCenter takes over the control) ?
Please answer ASAP.
Thanks
Hi
If you can now authenticate users against AD when the logon with the webclient and they get to see your vCenter Server and VMs, than you can be sure it is working properly.
To authenticate users from other domains, you need to add the domain controllers from that domain in your SSO just like you did with the first domain. Unfortunately SSO can’t understand child domains, so you would need to add each domain separately. In the last image from my instruction you see my domain “vanzanten.local”. You should see your domains in that list when you’re done. By clicking UP and DOWN errors you change the search order. If a user doesn’t specify the domain name, they account will be searched in the domains in this order.
Hope that was ASAP enough ;-)
Gabrie
—
Gabrie van Zanten
http://www.GabesVirtualWorld.com/
Skype ID: gabrie.van.zanten
Thanks Gabrie,
Ya that was real quick enough
I have got some more doubts on what you said , when i go to web client I cannot see SSO tab but i think all other features are working, so my doubt is whether there will be a SSO tab in the web client by which you can confirm that SSO is installed.
Also can you email (jerry.winlive@gmail.com)me the steps for the complete installation of vCenter 5.1 and how to add the domains for my handy reference, if so it would be so appreciated .
Thanks
Hi Gabrie, you made my day! I was frustrated with the SSO being unable to find the identity source during installation in my home lab and your post solved all my problems. Thanks again!