I hope you enjoyed part 1 and part 2 of my VMware vCloud networking series. At least I learned a lot from writing these posts and I have now much more confidence in being able to deploy a vCloud environment. In this part I’m going to explain how to publish a Web Site from a vApp to the outside world (my home network) and since it would also be nice to manage that server remotely I would like a RDP connection to that Windows 2012 Server.
The Plan
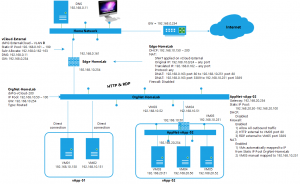
Starting point is the network design delivered in part 2. The task:
- Add a new Windows 2012 VM to the existing vApp-02
- Make the VM accessible from the home network (external network) and the organization network over ONLY the RDP and HTTP protocol
The following design shows the addition of the VM in the shaded area. All other data is from part 2.
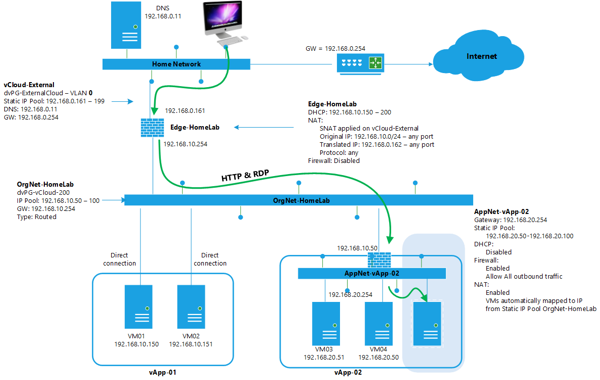
The vApp network
To add the Windows 2012 VM, installed the VM in the vSphere environment and when done import the VM into the Catalog and then go to vApp-02, click the virtual machines tab and click the big plus sign to add a new VM. Select the VM to add, click next, select the storage resources, click next and on the virtual machines screen select the desired network which is the AppNet-vApp-02 network and choose for “Static IP Pool” assignment. In part 2 we have created the AppNet-vApp-02 network and defined a static IP pool with an IP range of 192.168.20.50 – 192.168.20.100. This new VM will get an IP address from that pool.
In the next step “Configure Networking” make sure the AppNet-vApp-02 network is present and NAT and Firewall are enabled. Click finish to close the wizard. Now go to the “Networking” tab of the vApp. Right click the AppNet-vApp-02 network and choose “Configure Services”. Go to the “Firewall” tab. To be able to pass IP traffic from the outside to the VM, we need to create two new firewall rules:
- Allow HTTP traffic from EXTERNAL Source IP and ANY source port with destination port 80 and redirect it to the new VM
- Allow RDP traffic from ANY Source IP and ANY source port with destination port 3389 and redirect it to the new VM
Note: Pay attention to the fact that the source port is ANY and the destination port is 80 or 3389, basic network theory.
To build these rules click “ADD” on the “Firewall” tab and then add a rule like this (screen shot below). Pay attention to the keywords you can use, for example: “any”, “internal”, “external” and of course the IP address or range. Also see the red circles I drew in the image, when you click the icon there you can select the VM, isn’t that convenient!!! Use the icon by clicking on it, select the VM and NIC0 and don’t forget to change the “Apply Rule” to the NAT-IP. You need to use NAT IP here since the traffic will be arriving for the IP published on the outside of the vApp network, which is an IP address in the OrgNet-HomeLab 192.168.10.x range.
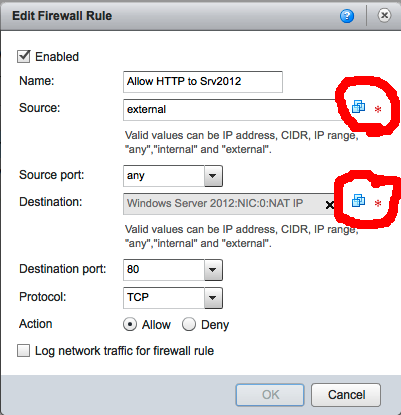
After both firewalls rules have been added, a NAT rule should be created on the “NAT” page. Maybe the new VM is listed already with a mapping mode of “Automatically mapped to”, but then you don’t have the assurance that the VM will always have this IP. For the NAT and Firewall rule that is no problem, but for it is not convenient if the outside IP can change all the time since other configurations like the EdgeGateway will be pointing to that IP. So add or change the mapping mode to “Manual” and enter an external IP valid for the OrgNet-HomeLab which is in the 192.168.10.0/24 range. In my example I picked 192.168.10.251. Now click OK and finish to save the configuration changes and don’t forget to press APPLY to make the new config changes active.
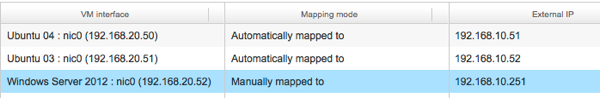
With this configuration, traffic coming from the OrgNet-HomeLab and destined for 192.168.10.251 port 80 or port 3389 will be allowed by the firewall and redirected to Windows Server 2012 VM. But that is not our complete mission for today. The next step is to make it possible to reach the VM from the external network, my home network. As you might expect, configuration changes have to be made at the EdgeGateway and the connection from Edge to OrgNet-HomeLab.
First an extra IP is needed at the outside (external network) of the Edge-HomeLab. Go to Virtual Datacenters under the “Administration” section and open the “OrgVDC-HomeLab”. Click the “Edge Gateways” tab and open the properties of the Edge-HomeLab. Click the “Sub-Allocate IP Pools” tab and change the current Sub-alloction of 192.168.0.162 to the new 192.168.0.162-192.168.0.163. Click OK to save then right click the Edge-HomeLab gateway and go to “NAT”. Here we need a Destination NAT rule that says that traffic coming in on 192.168.0.163 port 80 or 3389 should be redirected to external IP of the vApp, which is 192.168.10.251. Two rules are need, one for port 80 one for port 3389. See the screenshot:
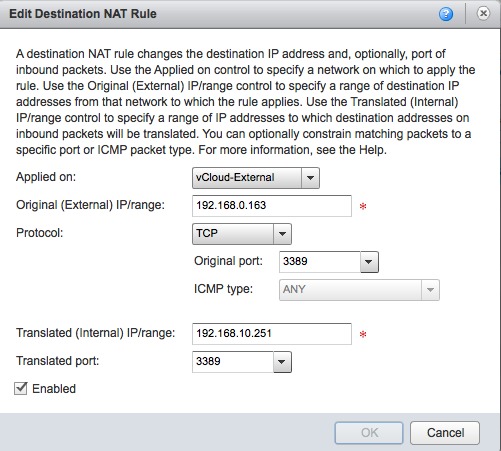
In the first part of this series where I created the Edge Gateway “Edge-HomeLab” I had disabled the firewall, so there is no need to add any firewall rules here. But I’ sure you will now be able to create a more secure configuration yourself….
After building the DNAT rules we’re done. To test the configuration start the new VM in the vApp and try o access it over RDP and HTTP from the external network. This is how the whole configuration should look now:
Overview of this VMware vCloud 5.1 Networking for dummies:
We don’t have that fancy “Pick your VM and its NIC” option in our firewall edit box. What version has that? We’re running vCloud director 5.1.1.
There is a difference in the firewall on the Edge or firewall on the vApp.
Gabes, thanks for your explanations. Is it possible to connect VMs to the ORG net and publish the website of this VM to the outside world? It’s like your part3 but without the vapp edge router.
Yes. Use the firewall / NAT rules on the Edge to publish the website.
Hey Gabes .
Thanks for your details explanation . I learned so much from your post .
But without luck , the DNAT configuration is not worked for me no matter i disabled it or enabled it , nothing happened ( For both vOrg NAT and the vApp NAT ) . I can ping the machine from vApp network ( 192.168.8.X )to my external network(192.168.1.X) . but not vice versa ..
I can ping the machine from vOrg network (192.168.4.X ) to my external network (192.168.1.X)
and vice versa .
Thanks .
Eric.